A solid policy is built with straightforward rules standards and agreements that conform to industry best practices and regulatory requirements.
Information security program template.
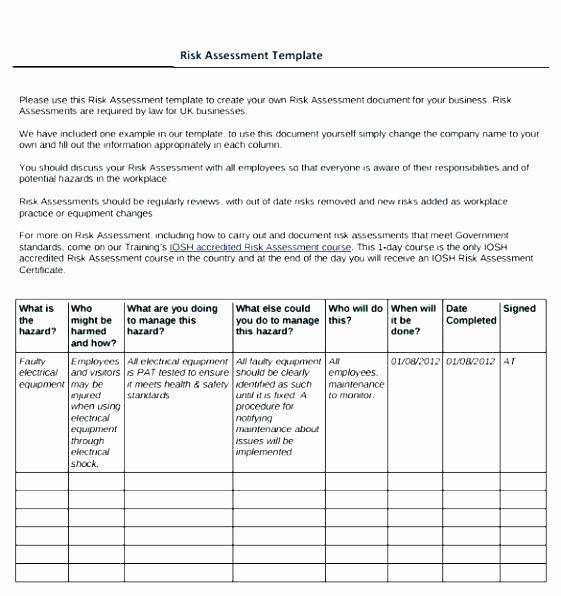
The information security policy template that has been provided requires some areas to be filled in to ensure the policy is complete.
42 information security policy templates cyber security a security policy can either be a single document or a set of documents related to each other.
This article outlines an incremental approach to rolling out an information security program.
Sans has developed a set of information security policy templates.
It may be necessary to make other adjustments as necessary based on the needs of your environment as well as other federal and state regulatory requirements.
But it s important to understand how your policy will fit into a greater security strategy.
These are free to use and fully customizable to your company s it security practices.
Available resources for a template to complete the information classification activity.
Refer to appendix a.
Additionally a sample is provided.
Its scope is a bit wider than just writing an information security policy itself.
An incremental approach to building an information security program.
It contains a description of the security controls and it rules the activities systems and behaviors of an organization.
Our list includes policy templates for acceptable use policy data breach response policy password protection policy and more.